Aarc x Lit: Powering OmniChain UX with Interoperable Accounts
Use Aarc's OpenAuth Kit to simplify onboarding for web3's first billion users.

The transition from Web 2.0 to Web3, fueled by Web3 technology advancements, has brought numerous L1 blockchains, L2 Rollups, Appchains, and dApps. Yet, this evolution leads to usability issues; users struggle with dApps spread across chains, fragmented liquidity, and multiple wallets.
Despite the availability of many crypto wallets, user base growth is slow, only doubling from 40 to 80 million from 2019 to 2022. In contrast, platforms like TikTok saw a massive increase in the same period. With six million daily users, Web3 adoption faces significant obstacles.
Hurdles like wallet interoperability, onboarding friction, and asset fragmentation hinder Web3 adoption. For the potential of omnichain dApps—effortlessly hiding cross-chain complexities—to be realized, wallets' fundamental operation must be reimagined to operate quietly, similar to Web2 applications. Web3 users face challenges and obstacles to widespread adoption. These include:
1.) Key Management is a Challenge
Accounts are crucial in the Ethereum ecosystem for holding assets, network interaction, and identity establishment. However, they vary in type, primarily comprising Externally Owned Accounts (EOAs) and Contract Wallets.
EOAs are the most prevalent account type. Identified by a 42-character string starting with "0x" - the private key, they pose a challenge for Web 3 Wallets. Users are solely responsible for managing and memorizing these private keys, a significant hurdle for those unfamiliar with cryptographic concepts.
The situation is severe: if you lose or forget your private key, your assets are unrecoverable. There are numerous accounts of people losing substantial funds due to misplaced or stolen seed phrases.
2.) Multiple Fragmented Wallets
The expanding Web3 ecosystem encounters difficulties in managing keys and seed phrases. Solutions such as social login and third-party wallet redirects simplify this process. Users can sign in through familiar platforms like Google and Twitter, eliminating the need to manage seed phrases. While this improves the onboarding experience, it may lead to unnecessary wallet creation and fragmentation.
For instance, a user might sign up for two different dApps, each using different authentication methods for wallet creation, such as ABCAuth for dApp A and ABCAuth for dApp B. Even if the user uses the same email address for both, two separate wallets would be created for each dApp. This results in assets and liquidity being spread across the ecosystem.
Fragmentation greatly impedes Web3 wallets' interoperability across blockchains, disrupting user experience and limiting Web3's potential. Addressing this is key to enhancing user convenience and fully leveraging decentralized technologies.
3.) Inconsistent Wallet Addresses
Each blockchain has unique rules and technologies, often resulting in different wallet addresses for each network. This can make the user experience challenging, particularly for those using multiple dApps on various platforms. Users must manage several credentials and multiple wallets, making transactions more complex and obstructing seamless interoperability—the primary motivation to make the accounts interoperable and omnichain.
4.) Custodial Wallets are not a solution
Custodial wallets offer crypto-to-fiat conversions, bill payments, and instant trading, often making them more appealing than non-custodial alternatives. Additionally, custodial wallets provide account recovery options, which can help users quickly regain access to their accounts in case of lost passwords, alleviating concerns about losing private keys.
However, this approach has significant drawbacks. It requires trust, contradicting blockchain's principles and Web3's objective of eliminating intermediaries. Custodial wallets stray from this path, asking users to rely on providers to safeguard their assets.
Privacy also becomes a concern. Many such wallets require identity verification, which can deter privacy-conscious users and potentially discourage signups due to the need to submit confidential information.
Introducing the Aarc OpenAuth Kit
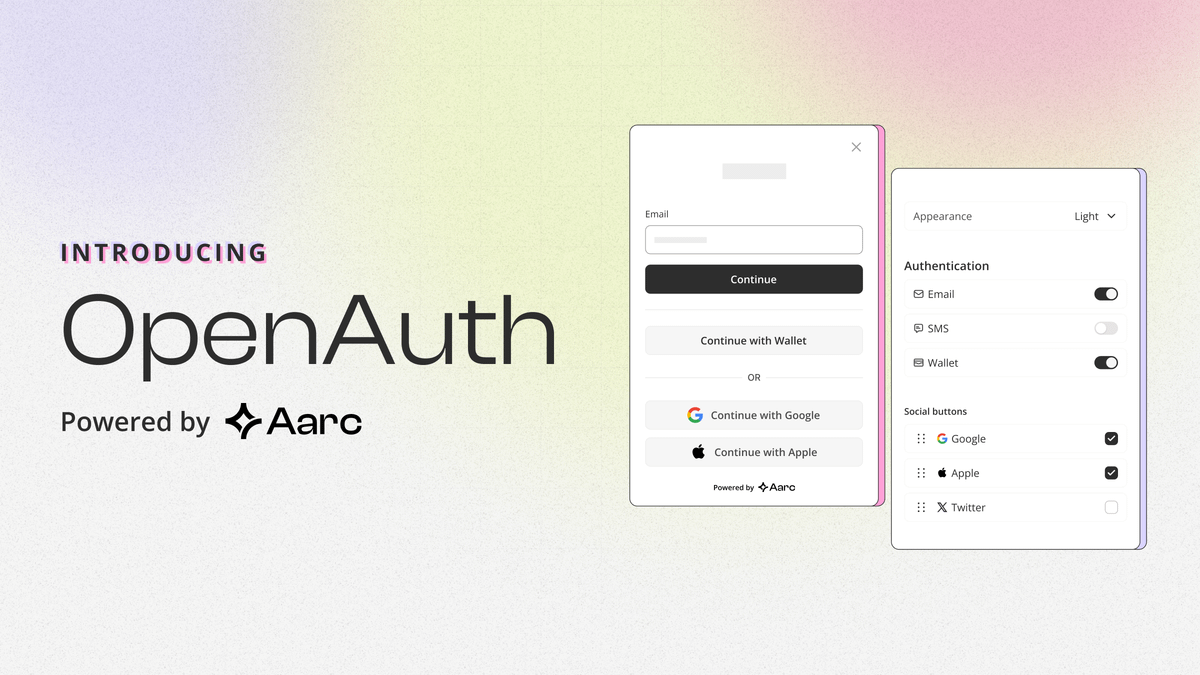
At Aarc, we are building a permissionless and modular rollup to unify the fragmented Web3 ecosystem and enhance interoperability for users and developers.
By unifying user account addresses using OpenAuth, we're one step closer to an overall unified user experience.
The OpenAuth Kit is one of three foundational infrastructure kits that streamline the user onboarding process without adding fragmentation. This kit further promotes the development of smooth omnichain dApps. With the OpenAuth Kit, users can deploy an interoperable address using any social authentication, like Google, Twitter, Discord, Facebook, Mobile, and Fascaster, all secured by multi-party computation (MPC).
How does Aarc OpenAuth operate?
Aarc OpenAuth uses the Lit Protocol to generate Programmable Key Pairs (PKPs) via Distributed Key Generation (DKG). With this approach, multiple Lit Nodes work together to form a new public/private key pair, ensuring no single node can access the complete private key.
Aarc OpenAuth first checks if a PKP exists within the Lit network when a user signs in. If not, it creates a new one. If a PKP already exists, the user is authenticated using methods associated with the PKP, such as wallet addresses or OAuth.
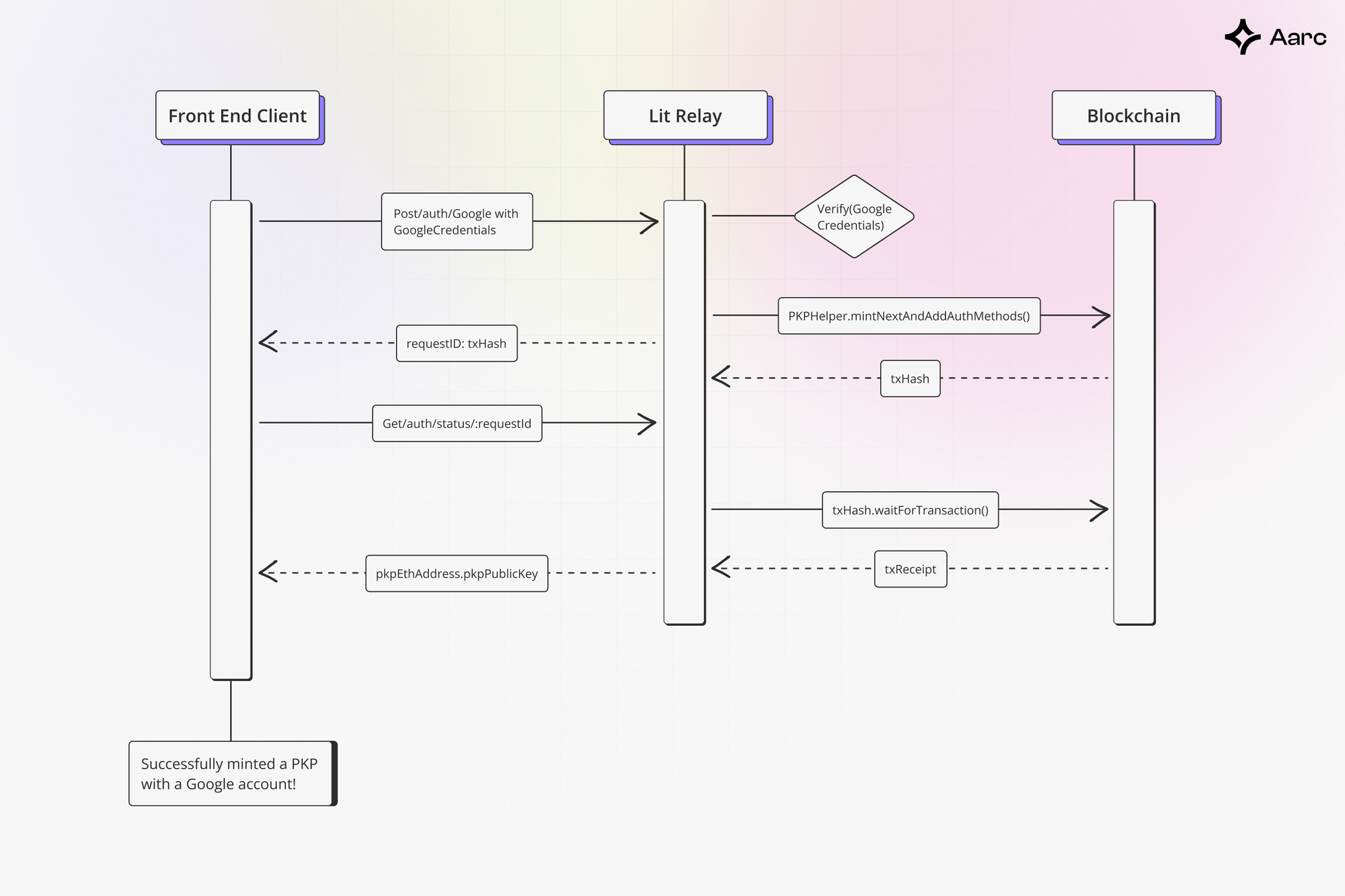
During authentication, the Lit network coordinates the interaction between the PKP and the custom authentication logic, defined in Lit Actions.
Lit Actions are JavaScript programs that establish signing and authentication logic for PKPs. The Lit Protocol’s open-source relayer aids in PKP minting and transactions. Each node in the network simultaneously processes the operation, ensuring all security requirements are fulfilled before granting permission.
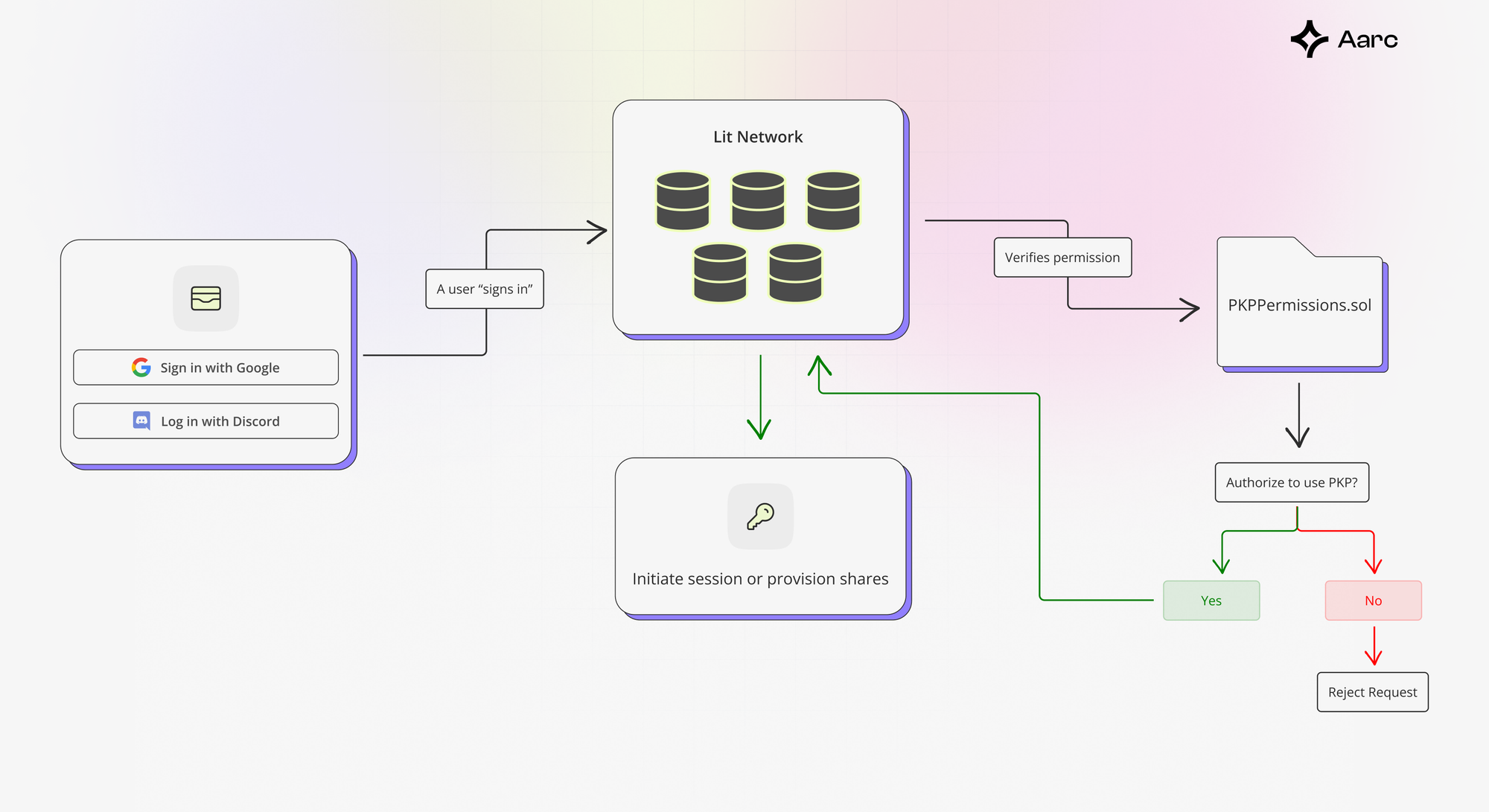
Upon successful authentication with a social login provider such as Google OAuth, SessionSigs are generated. These signatures stem from a randomly created ed25519 keypair in the user's browser and are stored locally. The payload of the AuthSig obtained during the authentication process includes the public key from this session key pair before. These keys are subsequently used to sign transactions and messages initiated by the user, which are broadcast over the blockchain.
What can be done with the OpenAuth Kit?
Aarc's OpenAuth Kit is a focused solution for evolving authentication, authorization and interoperability needs, enhancing security and simplifying integration.
1.) Streamlined Single Sign-On (SSO)
Aarc Open Auth introduces a robust Single Sign-On (SSO) feature that maps email addresses as unique identifiers. This SSO feature ensures that users keep the same public address when signing in via Twitter, Google, SMS, or phone, as long as they use the same email for authentication. This not only simplifies the login process but also significantly enhances the reusability of user addresses.
2.) Interoperability without Vendor Lock-in
The Aarc OpenAuth kit provides backward compatibility with the Lit Protocol. This feature enables users with an existing Lit account, created using any frontend SDK on another dApp or platform, to use the same address to sign into new dApps that utilize Aarc Open Auth, eliminating the need for a new address.
Existing users with a wallet address originally configured to use PKP on the Lit Protocol function seamlessly for message and signature creation when they access a new platform adopting Aarc Open Auth. This continuity is maintained as long as the social address to which PKP is mapped remains unchanged.
3.) Session Keys
The OpenAuth kit employs the Lit Protocol’s MPC network, which can function as default session keys after successful authentication. These temporary cryptographic session keys allow dApps to confirm transactions without continuous user signatures, enhancing the user experience.
4.) Unified Access with WalletConnect and other Aggregators
Aarc OpenAuth integrates seamlessly with WalletConnect. This allows users to access their Aarc-made user addresses through WalletConnect on dApps that have not directly incorporated the OpenAuth API/Widget. This feature consolidates all authentication processes onto a single screen, enabling users to select their preferred login method without leaving the UI.
5.) Multiple Supported Login Providers
With Open Auth, a dApp can authenticate users and create user accounts via multiple OAuth providers. These include:
- Email, authenticated via a one-time password (OTP) sent to the user's email address
- Phone number, authenticated via a one-time password (OTP) sent to the user's phone number
- EOA Wallet, authenticated via the Sign In With Ethereum (SIWE) standard
- Web2 social accounts (Google, Apple, Twitter, Discord)
- Farcaster accounts, authenticated via the Sign In With Farcaster (SIWF) standard
6.) Customisable Modal and In-dapp Wallet Manager
The OpenAuth Kit includes a customizable widget modal. This allows developers to adjust the look and function of authentication pop-ups to meet the particular needs of their dApps. Furthermore, OpenAuth Kit provides an In-Dapp Wallet Manager. This flexible light client can be fully tailored to dApp requirements, improving the user experience by letting developers adjust the wallet's interface and functionality to meet specific needs.
7.) In-built Key Rotation for extra security
To enhance security further, the OpenAuth kit implements key rotation for PKPs. Key Rotation involves programmatically generating new key shares with nodes, retiring old ones, and seamlessly updating related configurations and authentication logic. This ensures the integrity and security of user data and transactions.
Getting Started
The Open Auth Kit is now live, and you can try it out here.

