Lit Protocol: A Primer
Learn about how Lit Protocol works under the hood.

The development teams behind Lit Protocol are driven by the following north star question: How can we make it easier to build the user-owned web and financial system, without sacrificing on security and decentralization?
This primer covers the core architecture behind Lit Protocol, beginning with the dissection of the Lit Node, expanding to show how each node interacts with one another as a part of a distributed network, and finally how the Lit network interacts with individuals, protocols, and the internet as a whole.
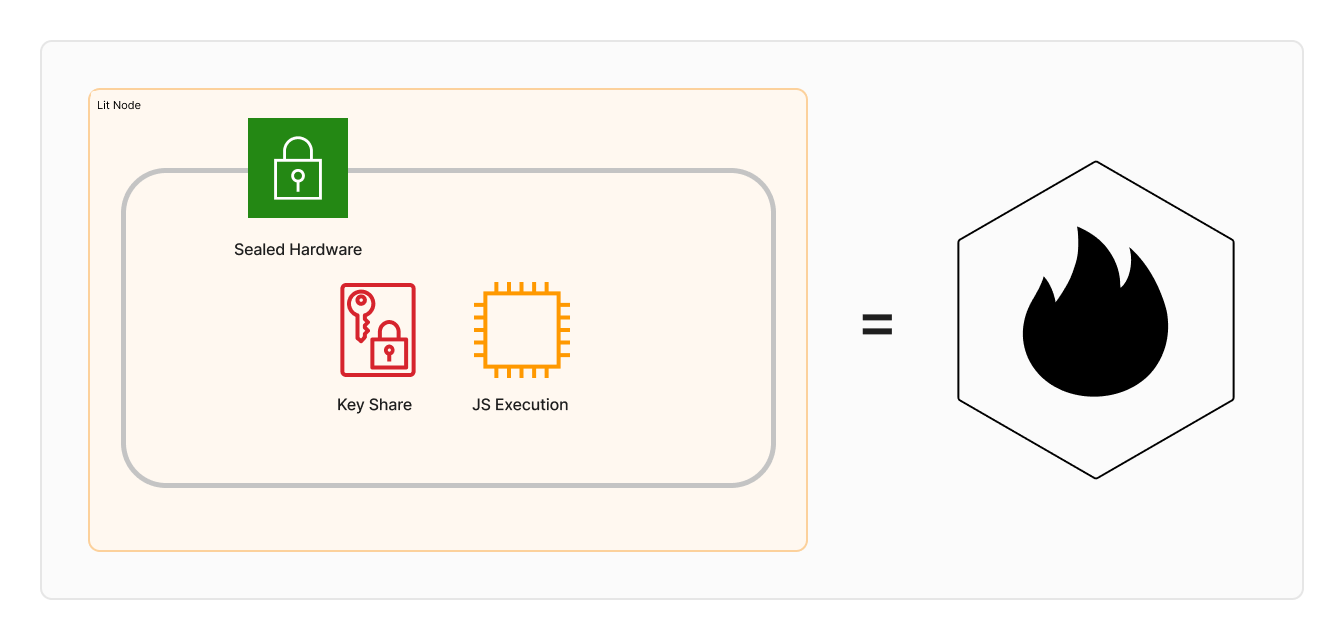
Lit Node
Each Lit Node is a sealed encrypted virtual machine running on an independently operated server. Here, “sealed” means that neither the operator of the Lit Node nor any other party can access the interior of the processor.
Each sealed node contains a JavaScript execution environment and key share(s).
Zooming out to help visualize this, each hexagon will represent a Lit node:
Lit Network
The Lit Network is composed of a collection of Lit Nodes that interact with each other in two main ways:
- The nodes check the “seal” of the other nodes in the network via a cryptographic proof (ensuring each node they interact with is “authentic”.)
- Each Lit node holds a number of independent key shares, each corresponding to a given threshold key pair managed by the Lit network. Each threshold key is created via distributed key generation and using these keys (i.e. requesting a signature) requires participation from at least two-thirds of the network, where each node is required to compute an authorization from within their sealed environment.
This two-thirds threshold is illustrated in the graphic below:
Zooming out even farther, we’ll use the Lit word-mark logo to represent the entire Lit network:

Lit x Users
Here, “users” are any entity that can be represented by a public blockchain address, including individuals, smart contracts, and organizations.
- The sealed keys managed by the Lit Network can be used as crypto wallets accessed via social and multi-factor authentication.
- Lit keys can be used to encrypt user data. This data remains completely confidential, only accessible to those who meet the selective disclosure rules you set.
- Users can delegate authority to use their keys to Lit Actions — private and immutable programs that can be used to sign, encrypt, and compute based on arbitrary rules you set.
Lit x Blockchain
Blockchains are decentralized ledgers that maintain an ordered history of accounts and their transactions. Lit can be used to interact with blockchains in several ways:
- Lit keys can be used to sign transactions that write data to blockchains.
- Blockchains can store the access control rules that Lit will read to grant decryption rights to private data for authorized users.
- Smart contracts or on-chain events can be used as a trigger for Lit, which can read and write data from anywhere, including other blockchains.
Lit x Storage
Storage networks act as global replicated pin boards.
- Lit keys can be used to sign transactions that write data to storage networks.
- Data encrypted with Lit can be stored privately on these open networks, with access control conditions being used to manage access.
- Lit Actions can be stored on these networks to be made immutable.
Lit x Internet
The internet contains data, event triggers, and web pages that Lit can read or alter using an API.
- Specific online events (accessed via API), can be used to trigger a transaction on Lit.
- Online data can be used as an access control condition that Lit reads to grant decryption rights to authorized users.
- Lit nodes can read and write data (via API) from within their trusted execution environment.
Get started building on Lit
Hopefully now you have a better idea of the architecture that underpins Lit Protocol.
Our mission at Lit is to provide developers with the tools they need to make the web3 vision for the future more attainable, making it easier for developers to build apps that put users in control.
If you’d like to build with Lit, get started here or get in touch to learn more.
If you’re interested in joining the team, check out these open roles.
It’s time to Free The Web.

