Decentralized Agent Stack

Using Crypto, From an LLM's Point of View
The convergence of Large Language Models (LLMs) with decentralized infrastructure is driving a generational shift toward intelligent autonomy in software. Autonomy, a concept central to professional, personal, and ethical growth, acquires a new dimension in software agents—enabling systems to function independently, governed by code or the agent’s end user.
Building autonomous software requires understanding four foundational components of the stack:
>LLMs – the agent's "brain"
>Cryptographic keys – the agent's "accounts"
>Signing policies – the agent's “guardrails”
>Data – the agent's "view of the world"
Together, these components create a robust framework for secure and intelligent autonomous agents.
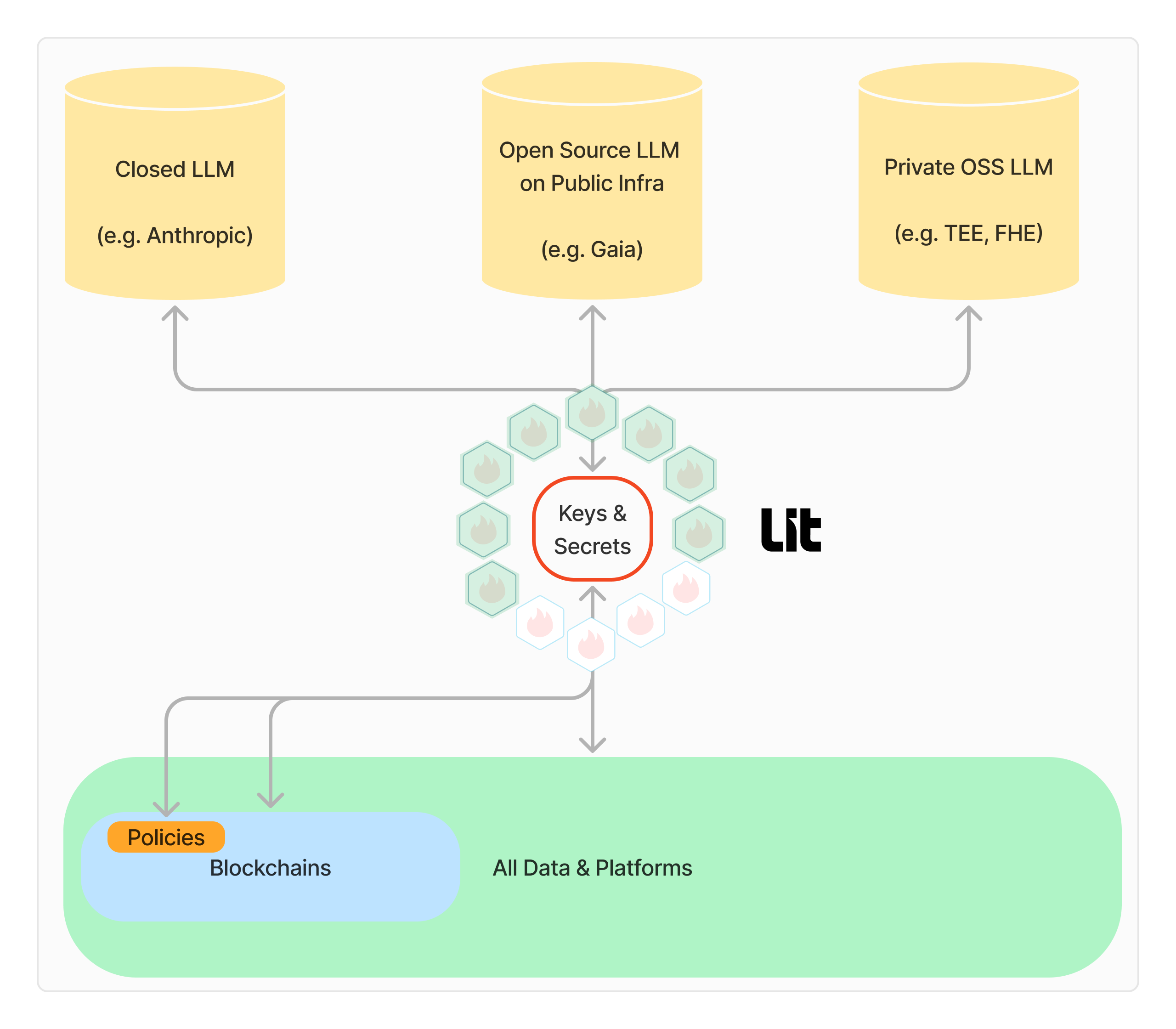
LLMs: Centralized, Decentralized, and Privacy-Preserving Architectures
Traditionally, LLMs have operated in centralized architectures, controlled by single entities managing training, deployment, and data. While efficient, this approach introduces risks: single points of failure and vulnerability to attacks as well as privacy concerns.
Emerging decentralized alternatives, such as inference networks that act as an "Airbnb for open-source LLMs," mitigate these risks. As LLM verifiability advances—providing proof of which model was run—public data can power autonomous decision-making in new, tamper resistant ways.
For private and distributed intelligence, technologies like Trusted Execution Environments (TEEs), Zero-Knowledge Machine Learning (ZKML), Fully Homomorphic Encryption (FHE), and Multi-Party Computation (MPC) enable secure, privacy-preserving LLMs.
With Lit Protocol, developers can interact with any LLM. API keys for LLM services are encrypted with the agent's decentralized keys (example). Teams can also run private LLMs on Lit Protocol’s devnet, which supports long-running compute in sealed TEEs.
Key Insight: While LLMs excel in semantic reasoning, they rely on external tools—like blockchains and software platforms—to access secrets such as API and cryptographic keys, in order to provide identity, accounts, and authentication across systems.
Cryptographic Keys: Empowering Agents Across Systems
Cryptographic keys serve as the agent's access points to decentralized systems. With a key, much like cash, control resides with the holder. For LLMs, keys enable secure communication, authentication, and interaction with digital assets.
In blockchain ecosystems, keys represent accounts for transactions and smart contract interactions. Managing these keys securely is critical since an agent developer who has control over the keys can steal funds. Lit Protocol addresses this through managing threshold keys across a network of TEEs to provide decentralized autonomy.
Lit Protocol also introduces programmability to key management, enabling agents to act autonomously within predefined boundaries. These capabilities integrate seamlessly with signing policies to ensure secure, programmable autonomy.
Signing Policies: Guardrails for Secure Autonomy
Signing policies define programmable rules governing cryptographic key usage. Acting as an agent's "authority," these policies can even lock out the agent's creator/developer if needed.
For example, signing policies can:
-Set spending limits
-Enforce time locks
-Block unauthorized transactions
-Require human approvals for high-value actions
Lit Protocol enables fully programmable signing policies, executed by a decentralized network of sealed TEEs. Policies can be:
-Immutable (stored on IPFS)
-Undateable (managed on-chain through multisigs or tokenized governance)
When deciding where to enforce your policy, it's crucial to balance security and flexibility to prevent vulnerabilities such as "rugging" agents through policy changes. Builders can get started with onchain governed agent policies here.
Data: The Agent's View of the World
Data is the agent’s world—what it perceives and interacts with. Blockchains, satellites, and your medical records are all data.For an agent to maintain privacy and autonomy, Lit Protocol enables encrypted data storage. Ciphertext (private, encrypted data) is stored on public infrastructure. Encryption keys are secured by the network, allowing agents to persist private state and manage user data without relying on centralized storage providers.
This decentralized approach allows agents to:
-Maintain sovereignty over their state
-Operate across public and private systems
-Use sensitive information, without trusted intermediaries
Agents equipped with Lit Protocol can uphold privacy while seamlessly integrating with broader ecosystems.
Get Involved
Passionate about developer tools? Join the Lit Protocol team and contribute to building the future of autonomous agents. Apply here!
Curious about building autonomous systems with Lit Protocol? Get started with Lit as a signer in the GOAT agent kit or check out the below video. You can fork the Lit Agent example from the video to create your first onchain agent policy and start sending autonomous transactions!

