Key Management and Identity Strategies for Crypto Agents
If you're building a crypto agent, understanding how to manage your agent's keys and identity is crucial. This guide aims to provide a structured approach to thinking about your agent's keys and identity, helping you make informed decisions about the underlying technologies and methods you choose.
- New to Crypto Agents? Start with this introductory post: Crypto Agents
- Need Background on Key Management and Decentralized Identity? Read this detailed analysis: The Evolution of Key Management
Understanding the Concepts
Before diving into the specific methods, it's important to understand the fundamental elements that will influence your choices:
- Method: The technique used for key management and identity.
- Provider: An example of a service or platform that leverages the method.
- Distributed Key Generation (DKG): Whether the secret material is distributed and not stored by a one company / person / computer.
- HOOL Automation: Stands for "Human Out of the Loop Automation," indicating whether the system can operate without user intervention.
- Autonomous: Whether the agent can operate independently without any user or developer intervention or dependence. In other words, is someone can pull the plug, it's not autonomous.
Overview of Agent Identity Methods
Here's a breakdown of different methods, along with their characteristics:
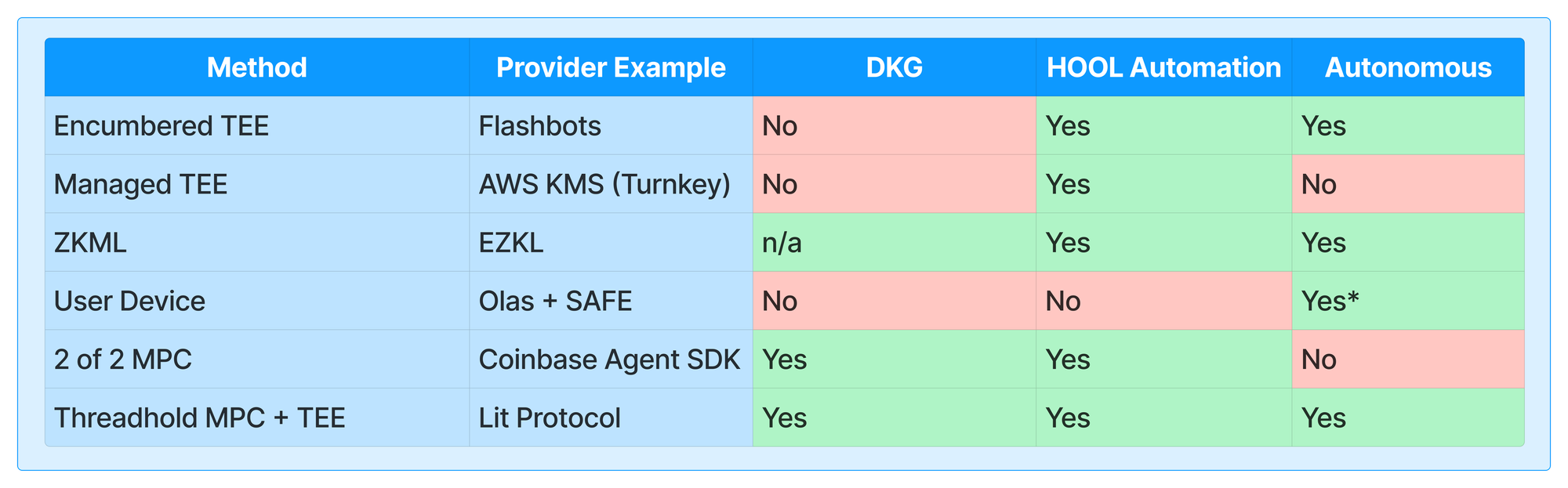
Method Details
Encumbered Trusted Execution Environment (TEE)
With this model, secrets are created and locked (encumbered) within a Trusted Execution Environment (TEE), which is a secure area within a single server's hardware. Because a TEE operates within a single physical server, any service provided by a TEE performs operations solely on that server. While TEEs allow for human-out-of-the-loop automation and enable the agent to operate autonomously, there is a real risk due to dependence on a single computer's operating system and material physicality. The digital assets managed using this method are reliant on the service provider as a potential single point of failure.
Managed TEE
Managed TEEs (e.g. key management providers built on AWS KMS) offer updatability at the cost of adding a closed source middleman. These services providers advertise themselves as "non-custodial wallets" when the rest of the statement is "non-custodial wallets for end users". It's tricky - the initial term is not referring to the custody model, but to the developers experience.
Agents built on these services have their assets reliant on the service provider. This introduces the similar regulatory uncertainties and security risks associated with updatable smart contracts, but in this case the logic is closed source. This method supports human-out-of-the-loop automation but lacks full autonomy since the agent can be censored by the service provider.
Zero-Knowledge Machine Learning (ZKML)
ZKML is a method that is highly secure and not dependent on a single computer. Proof generation running on coprocessors is resilient. This method supports both human-out-of-the-loop automation and full autonomy, allowing the agent to operate without any human intervention. The main trade-off is that it is slow and computationally expensive, which may impact performance and scalability for certain applications.
User Device
This approach relies on the user's device, making the security level contingent upon the user's operational security practices. If the user maintains good security hygiene, this method can be very secure. However, it places significant responsibility on the user. Automation is not inherent and is only possible when the device is switched on, indicated by the asterisk (*) in the table. Despite these limitations, the agent can operate autonomously under the right conditions.
2 of 2 Multi-Party Computation (MPC)
In this setup, the developer does not control the entire key material but controls the API that manages both parts of the key material. This introduces a dependency on human oversight, as the developer can influence the operation through the API. While it allows for human-out-of-the-loop automation, the method is not fully autonomous due to this reliance on human control.
Threshold MPC Network + TEE
Lit Protocol is a programmable, decentralized secret management network and open developer platform. It's the first and the only live threshold MPC + TEE network. By managing private keys and encryption keys with Lit Protocol, sensitive data is used in a threshold and blind compute environments, like to signing with private keys or using data accessed via API keys. The primary purpose of the network is to keep secrets safe and make it easy to use them with Lit Actions.
Lit Actions are serverless functions (JavaScript) that allow you to program with secrets and perform blind compute. Lit Actions can be stored on IPFS for immutability or on-chain for updatability. This flexibility means that agents can inherit attributes of smart contracts—being both immutable and updatable.
The security design of Lit Protocol employs a defense-in-depth approach by stacking two privacy technologies: Multi-Party Computation Threshold Signature Schemes (MPC TSS) and Secure Hardware (TEE). The main issue with MPC is the potential for collusion among parties, which the TEE helps prevent. Conversely, the main issue with a TEE is the single point of failure, which MPC mitigates. By combining these technologies, Lit Protocol offers robust security and resilience.
The TEE is also where you can run Lit Actions, including functions like fetch(), which opens up opportunities for agents to operate across Web2 platforms with private API keys as well as Web3 networks with crypto keys. This capability allows agents to interact securely and autonomously with both traditional web services and blockchain networks.
Lit Protocol aims to create the most powerful tool for developers seeking true autonomy or users who want control. Lit v0 was launched in February 2024 and updated to v0.1 in August. The network has processed >25 million requests for teams like Fox, Lens, and Genius.
Agents using Lit Protocol can operate fully autonomously without human intervention, benefiting from robust security, flexibility, and the ability to interact with both Web2 and Web3 environments.
Wrapping Up
Choosing the right key management and identity method for your crypto agent depends on your specific needs regarding security, autonomy, and operational efficiency. Methods like the Lit Protocol’s Threshold MPC Network combined with TEE offer strong autonomy and security, enabling agents to operate independently while interacting securely with various platforms.
On the other hand, solutions like the User Device method place more responsibility on the user but can be simpler to implement. Consider the trade-offs of each method carefully, especially concerning dependence on service providers, computational resources, and the level of human intervention required. By understanding these factors, you can select a key management strategy that aligns with your agent's goals and operational requirements.
If you’d like to start exploring Lit Protocol for your agent’s identity and secrets, get in touch, join the Lit Builders Circle, or read the docs:
