A Deep Dive into the Lit Ecosystem

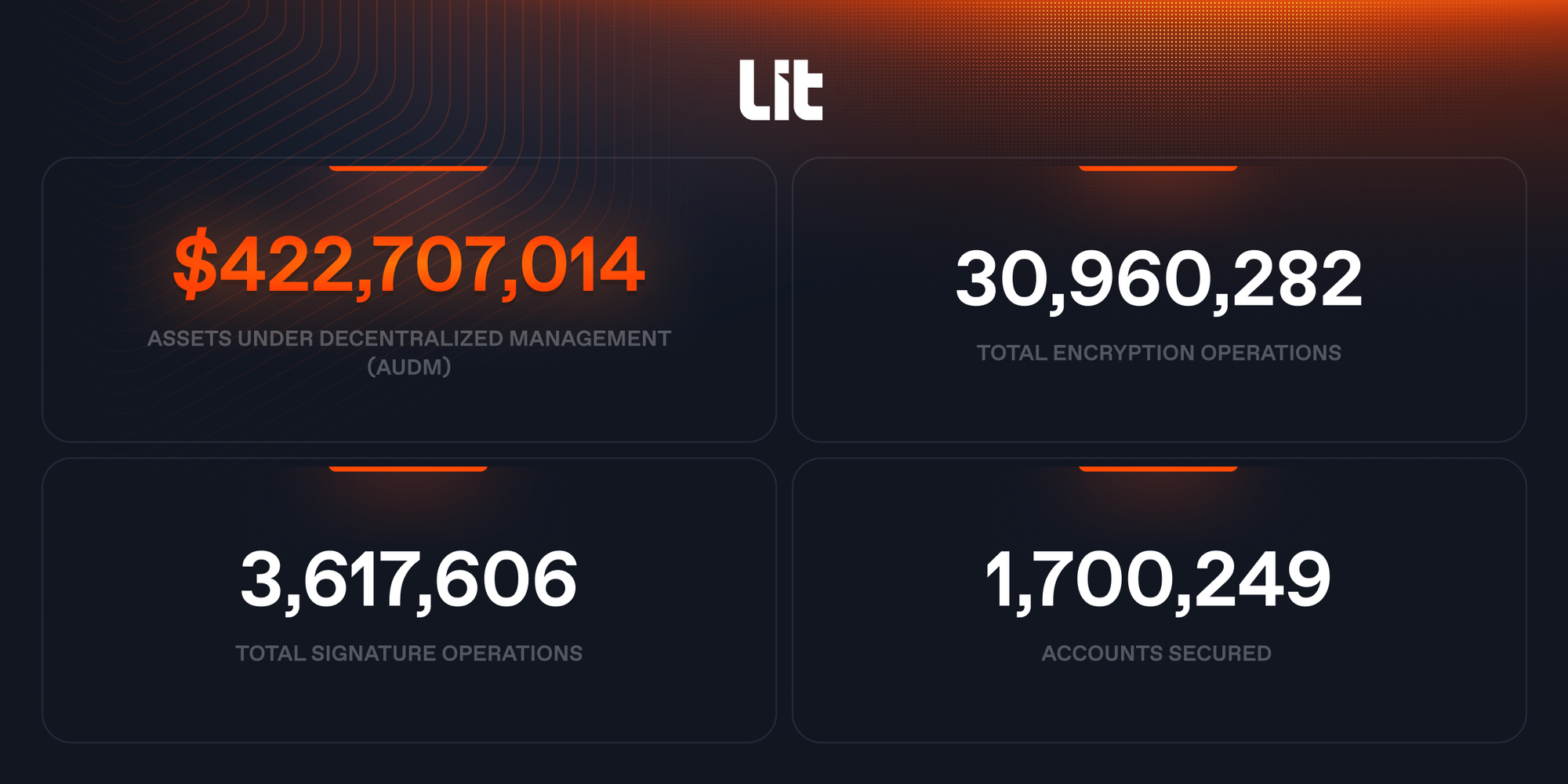
Lit Protocol is a foundational decentralized network for signing and encryption that’s powered by threshold cryptography, secure hardware, and blockchain technology. Lit Protocol v0 is currently securing more than $422M in assets under decentralized management (AUDM) and has signing requests growing at a rate of 45% / month. This traction is the result of a diverse ecosystem of products built on Lit Protocol, positioning the network as a leading infrastructure provider for all of crypto, AI, and beyond.
Most applications need one of two things to work:
- A signature to take action (send a transaction, authorize an API call, approve an agent to execute something).
- Encryption to secure data and control who has the ability to access it.
Today, both are usually handled through centralized custodians or locally stored private keys, which makes automation risky, cross-chain workflows clunky, and managing access to sensitive data vulnerable to exploitation. Lit replaces traditional key and secret management with a decentralized network that signs and decrypts based on programs that run within the network, rather than exposing keys or secrets directly.
That core function — programmable signing and encryption — has become the backbone of a growing number of live products using Lit Protocol in production.
This post highlights eight examples across four major patterns of usage.
Use Case Categories
Wallets & Smart Signers
Lit Protocol enables developers to build programmable, non-custodial wallets and signers that can execute transactions on virtually any blockchain while simplifying custody flows and simultaneously making them more secure.
This architecture powers next-generation wallets and protocols like CollabLand, Plurality Network, Human Wallet, and others which are all using Lit to facilitate decentralized account custody and onchain automation while keeping user control intact. The result is a secure and flexible signing and wallet management layer that supports both individual users and autonomous systems managing capital or digital assets in any ecosystem.
Cross-Chain Liquidity & Interoperability
Numerous protocols and applications rely on Lit to coordinate cross-chain transactions through programmable, policy-based signatures. By abstracting the underlying key material and allowing transaction execution to occur conditionally, developers can build systems that operate seamlessly across any blockchain including Ethereum, Solana, Bitcoin, and beyond.
Projects like Emblem Vault, Polaris, Tria and Genius are currently using Lit to automate complex DeFi operations that span chains, from liquidity rebalancing to token bridging and beyond. In each case, Lit serves as the universal signer that makes multi-chain activity both secure and programmable, eliminating the need for centralized relayers or bridges.
Agent Workflows
In order for AI agents to act on our behalf — executing transactions, retrieving data, or managing our assets — there needs to be verifiable guardrails in place to enforce what agents can and can’t do. Lit provides the foundation for that trust by letting agents perform operations under fine-grained, user-defined conditions without ever exposing keys or other sensitive data to the agent directly.
Lit Protocol’s Vincent framework was designed with exactly this use case in mind, enforcing policy-based signing and ensuring actions remain in-scope and verifiable. This approach enables a new category of agent-driven applications that can operate autonomously while remaining bound to human-defined logic and oversight.
Encrypted Data & Access Control
Lit extends beyond signing and wallet management to enable privacy-preserving collaboration and secure data management. Builders can use Lit for data encryption where access is enforced through flexible “Access Control Conditions” (ACCs), dictating exactly who, when, or under what conditions data access should be granted.
Projects like Humanity Protocol, Lens, and Molecule leverage Lit’s encryption and access control functionality to secure personal data, research information, and identity credentials across open networks. This ensures that sensitive information remains confidential by default, only becoming accessible under explicit, verifiable conditions. Lit’s model transforms privacy from a static setting into a programmable guarantee.
Featured Projects
Emblem Vault / Agent Hustle
Category: Wallet Management & Cross-Chain Orchestration
Emblem Vault has been building in the cross-chain DeFi space since 2016, creating products that simplify asset management, bridging, and automated DeFi execution. Its ecosystem includes Agent Hustle, a leading DeFAI agent on Solana that automates strategy execution for users. Both Emblem and Hustle integrate Lit to power signing automation, cross-chain orchestration, and secure user account management. By using Lit as the decentralized signing layer, they can coordinate actions across multiple chains without central custody or manual interaction.
Genius Terminal
Category: Wallet Management and Cross-Chain Orchestration
Genius Terminal aims to become the “on-chain Binance,” offering a powerful yet accessible DeFi trading experience for both beginners and advanced users. The platform supports cross-chain swaps, private transactions, and on-chain trading competitions through a unified interface. Lit provides the key infrastructure for cross-chain execution and user account management, allowing transactions to occur seamlessly across networks while maintaining privacy. Genius also uses Lit-managed keys to enable social logins, making it easier for new users to onboard without compromising security.
Tria
Category: Cross-Chain Orchestration
Tria unifies liquidity and user experiences across EVM and non-EVM chains, enabling gasless and seed-less cross-chain transactions through a chain-abstracted wallet and SDK framework. Lit is embedded in Tria’s infrastructure as its secure, chain-agnostic signing layer — enabling users to transact across virtual machines without manually bridging or holding multiple wallets. With Lit powering its cross-chain orchestration, Tria lowers technical barriers and creates a more seamless user experience for multi-chain asset movement and interaction.
Index Network
Category: Private Compute & Access Control Management
Index Network is an autonomous discovery protocol designed to connect users to relevant opportunities, communities, and collaborators based on shared data inputs. Using Lit’s encryption and access-control framework, Index enables secure data sharing between parties while ensuring that sensitive information is only revealed under consented conditions. This model allows users to retain ownership of their personal or professional data while being able to benefit from Index’s network-wide discovery and reputation system.
Polaris
Category: Cross-Chain Orchestration
Polaris uses Lit to facilitate cross-chain transaction orchestration, allowing users to express their desired intents and have them executed automatically across supported networks. Much like Genius, Polaris integrates Lit as its universal signing and policy engine, enabling secure cross-chain operations without requiring users to handle private keys or bridge assets manually. With Lit, Polaris simplifies what would otherwise be a multi-step, error-prone process into a single coherent user flow.
Eco
Category: Cross-Chain Orchestration
Eco is a stablecoin protocol focused on enabling seamless, interoperable payments across chains. By integrating Lit as a decentralized cross-chain signer, Eco can authorize stablecoin mints, burns, and transfers without relying on centralized custodians or intermediaries. This allows stablecoin transactions to remain verifiable and trust-minimized, while maintaining the flexibility needed for global payment use cases.
Molecule
Category: Access Control Management
Molecule is a biotech research and IP platform that tokenizes access to scientific data and intellectual property. Researchers, investors, and institutions can collaborate and share results transparently while maintaining strict control over sensitive datasets. Lit’s encryption and access-control system secures all proprietary documents, ensuring that only approved stakeholders — such as token holders or DAO members — can decrypt and view them. This enables trust-based collaboration within a permissionless, open environment.
Humanity Protocol
Category: Access Control Management
Humanity Protocol is building the proof-of-humanity layer for the internet, enabling any online actor to cryptographically verify their identity as a real human. To preserve privacy, Humanity uses Lit to encrypt the metadata associated with each verifiable credential issued by the protocol. This ensures that identity proofs remain valid and verifiable without exposing sensitive biometric or behavioral data. The result is a scalable, privacy-preserving system for establishing human authenticity in digital environments.
Closing
What unites all of these teams is simple:
They needed automation, account, or access management without surrendering control over keys or data.
Lit provides the tools to enable:
- Wallets that act without being custodial
- Agents that automate execution without being reckless
- Cross-chain flows that don’t rely on centralized relayers
- Data collaboration that doesn’t leak sensitive or private information
If you’re building in any of the categories above — or you’re building something that should be automated but can’t be without introducing additional trust assumptions — Lit is likely the missing layer.
Build on Lit
Explore the Ecosystem
Interviews with Lit Builders
